In this blog, let us look at one of the AWS services that everyone should know(who is willing to learn AWS) AWS IAM.
With AWS Identity and Access Management service(IAM), you can specify who can access your AWS services and resources.
Let us understand this AWS IAM in a detailed way with some examples.
What is IAM service?
IAM can be abbreviated as an Identity and Access management service. Using the IAM service, you can manage who can access your services in AWS and the resources present in the AWS.
Let us understand this with a simple example by considering College.
Generally, we will have security and security guards on our college premises. What these security people would mean, they only allow authorized people into the college.
Similarly, using AWS IAM service will grant the permissions to the users to access the services and resources.
Assume you are a student, you are authorized to enter the classrooms and specified laboratories only. You cannot enter the staff rooms and office rooms without special permission.
Similarly, college faculty are authorized to enter staff rooms, office rooms and classrooms as well.
If we compare the above scenario to our AWS IAM service. In the service, we can specify a certain role to each user and give their authorization policies.
Assume, there is an X company managing their AWS and they have users such as Developers, DevOps persons, Database administrators (DBA) and others.
Here Developers can only have the permissions to access the services which is used for developing and testing their applications such as EC2 instances.
DevOps person will have the complete authority to use all the services.
DBA can only have permission for the database-related services.
With this, we can understand that we can have role-based permissions using the IAM service.
IAM features:
There are many features for IAM service, some of them were:
Shared access to your AWS account: With a single AWS account, multiple users can access that account at the same time.
Granular permissions: As a root user(who has all the permissions), you can give permissions to the other users to access the services.
Multi-factor authentication(MFA): If you enable MFA, while a user is logging into the AWS account, he not only requires a password but also a code from a specially configured device.
Free to use.
Things to know in IAM:
In IAM service, there are three main things that you should know, they are Users, Policies, and Groups.
Users: Users are the ones that are mainly used for authentication. A user can enter into your AWS account.
Policies: Policies are the rules that are attached while creating users. It specifies what services and resources a user can access. These are like permissions.
Groups: The group concept is used to group some users and combinely give the policies to them. If we take an example, we can group all the developers and make a group of Developers, similar to Testers and so on...
AWS Security best practices
AWS IAM service is basically used to manage access to AWS resources, IAM is a powerful toolset to manage access to resources but sometimes it can be challenging to configure and manage. However, you can keep your AWS environment well-maintained and secure through some best practices such as
Enabling Multi-Factor Authentication(MFA)
Avoid using root user credentials for daily tasks
and there are many practices that everyone should know. If you want to know more about the IAM security best practices I highly recommend you to read the blog post written by Tobias Schmidt which is present on spacelift.io 12 AWS IAM Security Best Practices
Demo
Now let us have some demos on IAM like how to create a user, how to attach policies and test that user whether can access the services to which he doesn't have access.
To do this you have to have an AWS account. If you don't have an account create one and try this.
Firstly log in to the AWS console and in the 🔍Search bar, enter IAM, You will look similar to the below image. Click on the first IAM.

After clicking, you can observe the Dashboard like this
If you want to create a new User, click on the Users button which is on the left side
You will get the empty list when you click it. To create a user, click on the Create user button which is on the right side top corner.
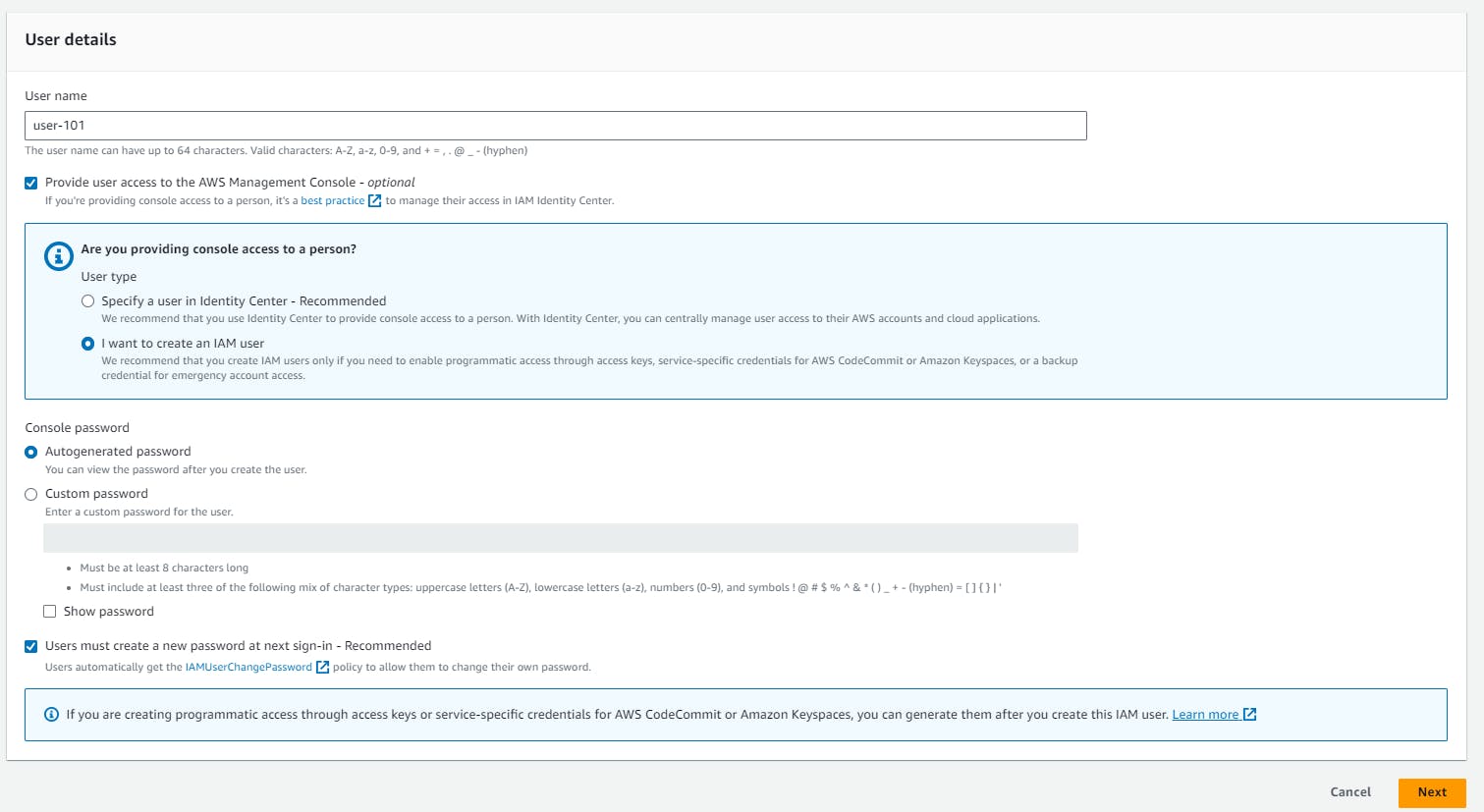
You will like this

I gave the user name as user-101, then ticked the mark on "Provide user access to the AWS Management Console - optional". You will ask a question like Are you providing console access to a person? there select "I want to create an IAM user", and keep the default setting as is. You can see my settings below.
As soon as you click the Next button, you will be asked to set permissions for this user-101 which would look like this:

Here there are three Permission options
Add user to group: This option doesn't grant any permission to the user that we are creating, but if we want this user to be added to any particular group, we can add him using this option.
Copy permissions: This option gives us the capability of copying the permissions of the existing users or groups.
Attach policies directly: With this option, we can attach the required policies to the user.
We have over 1100+ AWS manage permission policies present here. If we want to give any permissions to the user, we need to ask that user what services he actually requires or else there are 11 job function policies which is managed by AWS.
If you want to create a new permission policy, AWS provides that feature too.
Now let us give some permissions to this user-101, Assume he is from the financial department and let us give him AWS-managed - job function policy Billing. For this policy, he can have access to only 12 out of 386 services.

Attach him this permission and click Next. On the next page, you can review the user details and permissions attached to him. For my user, this review page is like this

Here with the Billing policy, we have the IAMUserChangePassword policy. This is because while creating the user, we opted for an autogenerated password and AWS has recommended that the user must create a password at the first sign-in. That's the reason, AWS has automatically attached this policy to this user.
When you click on the Create user button, a new user is created and details of that user will be given to you such as Console sign-in URL, User name, and Console password. To share with that user, you can download csv file too.

Now let us log in to this user. I am logging in through the provided URL. Once you go to the URL, you will be asked to enter the details like Account ID, username, and password.
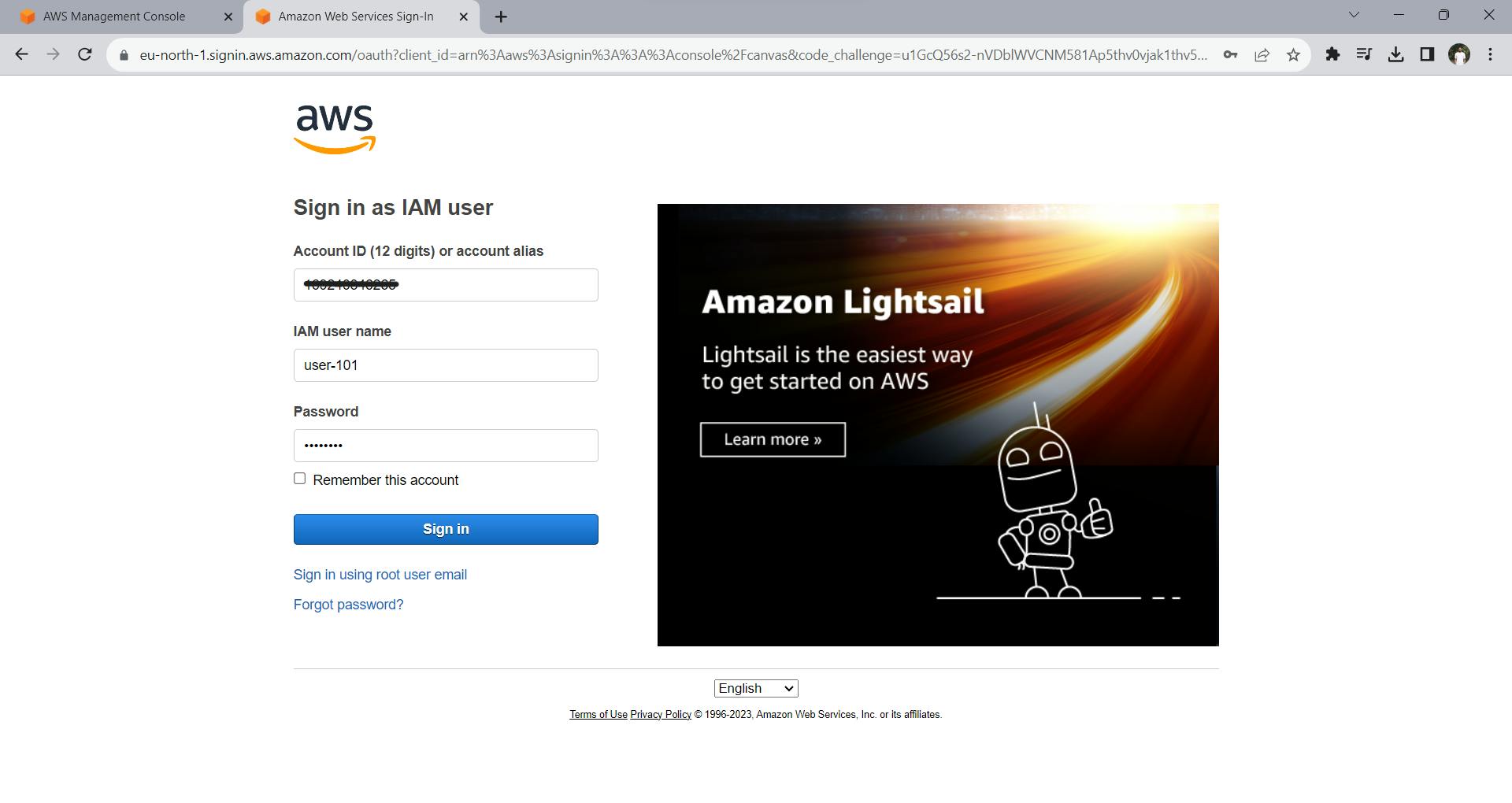
After clicking sign-in, you will be asked to change the password, change it you will be entered into the AWS console of this user.

That is it, You have created a user named user-101 with some policies like Billing🥳🥳. In a similar manner, if you want to create a user with some other permissions, you can create one with the same steps.
Now let us test whether you can access other services rather than the service mentioned in the Billing policy. Storage service S3 buckets are not included in the Billing policy, Let us look into that service by listing buckets.
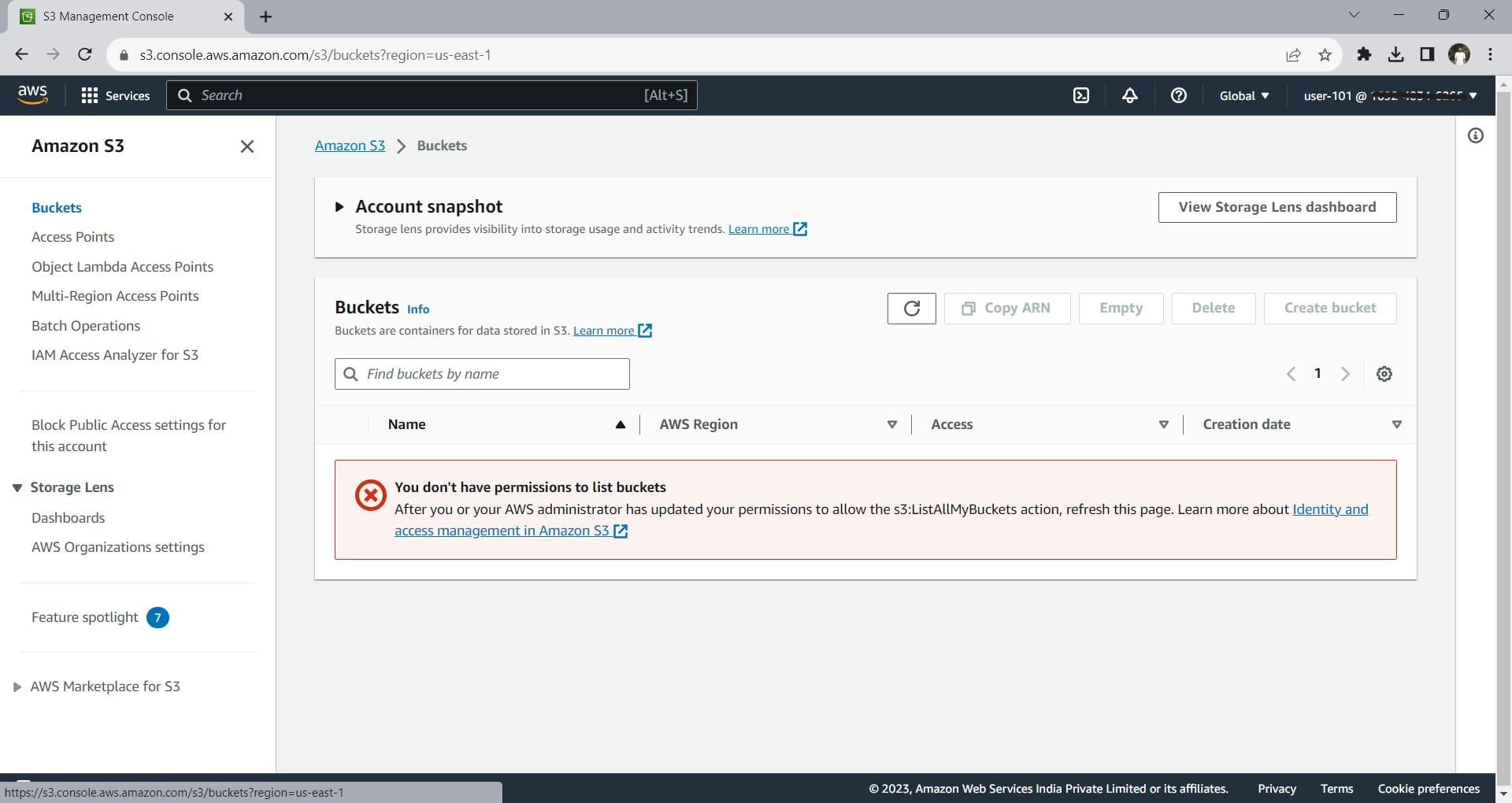
It is restricting us to view these resources present in this service.
This is how the AWS IAM service works. Have fun creating users and managing permissions for them. See you again in some other blog.
Thank you for reading😀😀.
